
According to the report of the Sysdig Threat Research Team, thousand of docker container images hosted on the popular database repository Docker Hub are malicious, putting users at risk of cyberattack.
Sysdig Threat Research Team performed an analysis of over 250,000 Linux images in order to understand what kind of malicious payloads are hiding in the container images on Docker Hub. The result they found was shocking as thousands of images contained nefarious assets such as crypto miners, backdoors, and DNS hijackers.
The Docker Library Project reviews images and verifies those it deems to be trustworthy, but there are plenty that remains unverified. Sysdig automatically scanned 250,000 unverified Linux images and found 1,652 to be hiding harmful elements.
"Sysdig Threat Research Team built a classifier to extract and collect information about recently updated images in Docker Hub to determine if those images contained anything anomalous or malicious within the image layers." - Sysdig says
What is Docker Hub?
Docker Hub is a cloud-based image repository in which anyone in the world can download, create, store, and deploy Docker container images for free. It provides access to public open-source image repositories, and each user can create their own private repositories to store personal images.
Docker Hub provides official images which are reviewed and published by the Docker Library Project, making sure that best practices are followed and providing clear documentation and regular updates. In addition, Docker Hub enables Independent Software Vendors (ISVs) via The Docker Verified Publisher Program. Development tool vendors in this program can distribute trusted Dockerized content through Docker Hub with images signed by Verified Publisher, reducing a user’s chance of downloading malicious content.
Categories of Malicious Images
Upon analyzing the number of unverified images Sysdig Threat Research Team several types of Dangerous Images in Public Registries, such as Typosquatting, Cryptominers, and Keys.
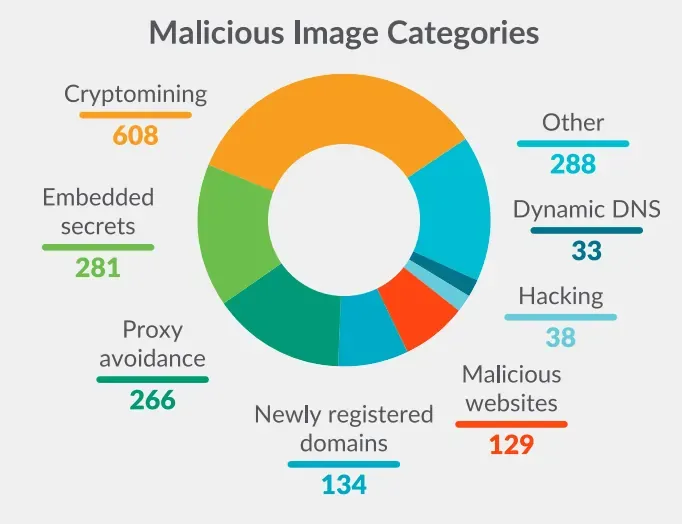
Cryptomining images were the most common malicious image type, present in 608 of its scanned images.
However, embedded secrets in layers are the second most prevalent, which highlights the persistent challenges of secrets management. Secrets can be embedded in an image due to unintentionally poor coding practices or this could be done intentionally by a threat actor. By embedding an SSH key, AWS credentials, GitHub, and NPM tokens. The attacker can gain access once the container is deployed. These were found in 208 of the images.
To prevent accidental leakage of credentials, sensitive data scanning tools can alert users as part of the development cycle.
Threat actors were using typosquatting as a tactic in compromised images - slightly misspelled versions of popular and trusted images in the hopes that potential victims will not notice and download their fraudulent version instead.
Sysdig claims that there has been a 15% rise this year in the number of images pulled from the public library, so it looks as if the problem isn’t going away anytime soon.
The Sysdig team recommends organizations deploying such workloads should ensure that they enact appropriate preventative and detective security controls that are capable of mitigating cloud-targeting attacks.