
According to the Python Package Index, threats actors are targeting PyPI users via a phishing email where the message of the email claims that there is a mandatory ‘validation’ process being implemented by Google, and invites users to follow a link to validate a package, or otherwise risk the package being removed from PyPI.
For clarification regarding the removal of the package, PyPI says-
PyPI will NEVER remove a valid project from the index. PyPI only removes projects which violate our TOS or are in some way determined to be harmful (e.g., malware).
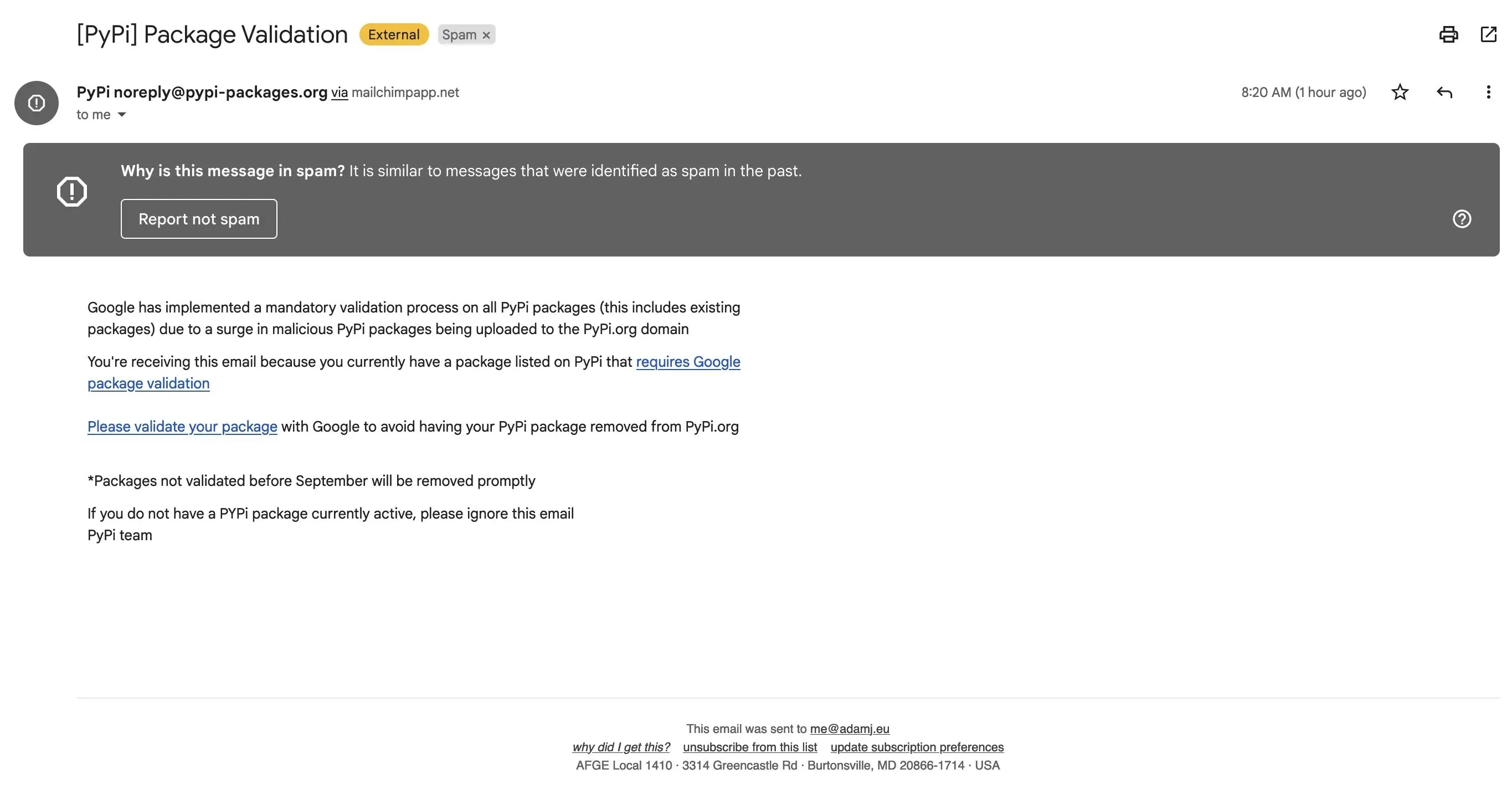 |
| Phishing emails sent to PyPI users |
When users click on the link provided on the email to validate the package (as per pish email), it takes users to the caricature PyPI's login page (sites[dot]google[dot]com/view/pypi/validate), which steals any credentials entered. It is unclear whether the phishing site was designed to relay TOTP-based two-factor codes.
When users enter the login credential, the phishing site sends the data to a URL on the domain linkedopports[dot]com. According to the whois data, the domain was registered 16 days ago.
It is yet not clear how many total users is been affected but PyPI noted that some maintainers of legitimate projects have been compromised, and malware was published in the latest release for those projects. In the meantime, PyPI has removed the releases of affected projects and also temporarily frozen the maintainer accounts.
The pattern followed by the Malicious Package
PyPi found that the malicious releases of the affected projects follow a similar pattern, of using the same domain name linkedopports[dot]com. For security concerns, PyPI has taken down several hundred typosquats that follow the same way.
 |
| malicious PyPI releases |
PyPI users need to Do
In the meantime, there are not many details about this credential-stealing campaign but if you believe you may have entered credentials on a phishing site, then immediately (1) reset your password and (2) reset your 2FA recovery codes. Furthermore, it is recommended to review your account's events and API tokens for suspicious activities.
While logging into your PyPI accounts, do verify that the URL in the address bar is http://pypi.org and that the site’s TLS certificate is issued to http://pypi.org. Additionally, consider using a browser-integrated password manager.
The accounts protected by hardware security keys are safe and to prevent phishing attacks from succeeding, do enable two-factor authentication 2FA on your accounts, ideally using hardware security keys or WebAuthn two-factor authentication.
PyPI is actively reviewing reports of new malicious releases, and ensuring that they are removed and the maintainer accounts restored. Additionally, PyPI is also working to provide security features like 2FA more prevalent across projects on PyPI.
Attacker Behind the Attack
According to the researchers, the gang's earliest campaigns were quite modest and involved the use of rogue Python installer applications that were used to deploy .NET-based malware called JuiceStealer, was used to extract passwords and other sensitive data from the victims' web browsers.
According to SentinelOne, linking the attack to a group called JuiceLedger, the attacks on PyPI package developers are the development of a campaign that started at the beginning of the year and was initially aimed at potential victims through fake cryptocurrency trading applications. A possible goal is to infect as many people as possible with info stealers through trojanized and typosquatting packages.