
If you are using Microsoft email service then you need to be careful. This is because Zscaler, a cybersecurity research firm, has discovered a new phishing ongoing campaign targeting Microsoft email users.
According to the Zscaler researcher threat actors are running a phishing campaign targeting corporate users and the campaign is being run using the adversary-in-the-middle (AiTM) technique to bypass multi-factor authentication (MFA).
The AiTM technique, as the name suggests, places an adversary in the middle to intercept the authentication process between the client and the server to steal credentials during the exchange, which leads to the theft of MFA details. Basically, the adversary in the middle acts like the server to the real client and the client to the real server.
To illustrates the AiTM phishing process Microsoft gave the diagrammatic view, check below —
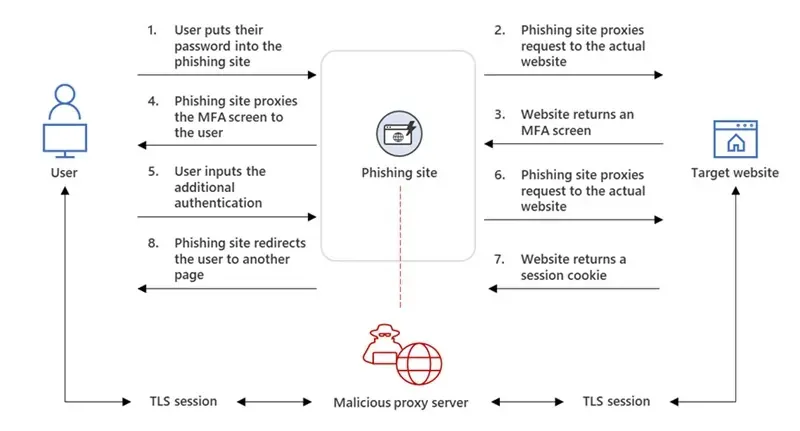 |
| AiTM phishing campaign and follow-on BEC (Source: Microsoft) |
The phishing page has two different Transport Layer Security (TLS) sessions—one with the target and another with the actual website the target wants to access. These sessions mean that the phishing page practically functions as an AiTM agent, intercepting the whole authentication process and extracting valuable data from the HTTP requests such as passwords and, more importantly, session cookies. Once the attacker obtains the session cookie, they can inject it into the user's browser to skip the authentication process, even if the target’s MFA is enabled.
The AiTM phishing process can currently be automated using open-source phishing toolkits and other online resources. Among the widely-used kits include Evilginx2, Modlishka, and Muraena.
Zscaler has summarized its research on this phishing campaign and its key points are—
- Corporate users of Microsoft's email services are the main targets of this large-scale phishing campaign.
- All these phishing attacks begin with an email sent to the victim with a malicious link.
- The campaign is active at the time of blog publication and new phishing domains are registered almost every day by the threat actor.
- In some cases, the business emails of executives were compromised using this phishing attack and later used to send further phishing emails as part of the same campaign.
- Some of the key industry verticals such as FinTech, Lending, Insurance, Energy, and Manufacturing in geographical regions such as the US, UK, New Zealand, and Australia are targeted.
- A custom proxy-based phishing kit capable of bypassing multi-factor authentication (MFA) is used in these attacks.
- Various cloaking and browser fingerprinting techniques are leveraged by the threat actor to bypass automated URL analysis systems.
- Numerous URL redirection methods are used to evade corporate email URL analysis solutions.
- Legitimate online code editing services such as CodeSandbox and Glitch are abused to increase the shelf life of the campaign.

attacker-registered domains which were typo-squatted versions of legitimate