
Microsoft says that they were tracking SEABORGIUM since 2017, and now they have taken actions to disrupt campaigns launched by threat actors. Its campaigns involve persistent phishing and credential theft campaigns leading to intrusions and data theft. SEABORGIUM intrusions have also been linked to hack-and-leak campaigns, where stolen and leaked data are used to shape narratives in targeted countries.
Who is SEABORGIUM?
According to Microsoft, SEABORGIUM is a highly persistent threat actor, frequently targeting the same organizations over long periods of time. Once successful, it slowly infiltrates targeted organizations’ social networks through constant impersonation, rapport building, and phishing to deepen their intrusion. SEABORGIUM has successfully compromised organizations and people of interest in consistent campaigns for several years, rarely changing methodologies or tactics. Based on known indicators of compromise and actor tactics, SEABORGIUM overlaps with the threat groups tracked as Callisto Group (F-Secure), TA446 (Proofpoint), and COLDRIVER (Google).
SEABORGIUM Targets
As Microsoft was observing SEABORGIUM for many years, the software giant noted that SEABORGIUM campaigns targeted over 30 organizations, including personal accounts of people of interest. They observed a consistent methodology from SEABORGIUM with only slight deviations in their social engineering approaches and in how they deliver the initial malicious URL to their targets. In this section, we provide a detailed analysis of SEABORBIUM’s operational tactics as well as several examples of their campaigns.
SEABORGIUM primarily targets NATO countries, particularly the US and the UK, with occasional targeting of other countries in the Baltics, the Nordics, and Eastern Europe. Such targeting has included the government sector of Ukraine in the months leading up to the invasion by Russia, and organizations involved in supporting roles for the war in Ukraine.
Furthermore, SEABORGIUM primarily focuses operations on defense and intelligence consulting companies, non-governmental organizations (NGOs) and intergovernmental organizations (IGOs), think tanks, and higher education. SEABORGIUM has a high interest in targeting individuals as well, with 30% of Microsoft’s nation-state notifications related to SEABORGIUM activity being delivered to Microsoft consumer email accounts. SEABORGIUM has been observed targeting former intelligence officials, experts in Russian affairs, and Russian citizens abroad.
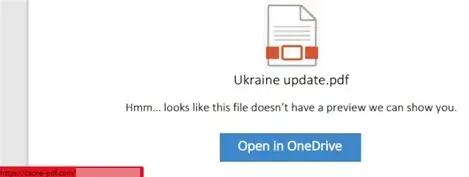 |
| Example PDF file used in campaigns |
SEABORGIUM mainly targets users or organizations via phishing campaigns for stealing users' credentials. They directly add a URL to the body of their phishing email or PDF file attachment that contains a URL. These attachments typically imitate a file or document hosting service, including OneDrive, and request the user to open the document by clicking a button. When the target clicks the URL, the target is directed to an actor-controlled server hosting a phishing framework. Occasionally, the actor leverages URL shorteners and open redirects to obfuscate their URL from the target and inline protection platforms.
Moreover, Microsoft has observed attempts by the actor to evade automated browsing and detonation by fingerprinting browsing behavior. Once the target is redirected to the final page, the framework prompts the target for authentication, mirroring the sign-in page for a legitimate provider and intercepting any credentials. After credentials are captured, the target is redirected to a website or document to complete the interaction.