
Microsoft uncovered a vulnerability in macOS that could allow specially crafted codes to bypass the App Sandbox protection and run restricted code on the system.
In the blog post, Microsoft detailed the vulnerability that is currently identified as CVE-2022-26706. Microsoft noted that the vulnerability has been fixed by Apple and was included in the security updates released on May 16, 2022.
Jonathan Bar Or of the Microsoft 365 Defender Resear ch Team explains that the vulnerability was discovered while researching potential ways to run and detect malicious macros in Microsoft Office on macOS.
Microsoft Word can read or write files with an “~$” prefix. Our findings revealed that it was possible to escape the sandbox by leveraging macOS’s Launch Services to run an open –stdin command on a specially crafted Python file with the said prefix. As seen in the screenshot of the syntax below, Word is allowed to read or write files with filenames that start with the “~$” prefix. The reason for this rule is rooted in the way Office works internally and remains intact for backward compatibility. - Jonathan added.
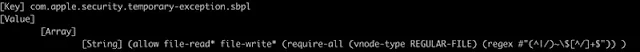 |
| Sandbox rule for Microsoft Word on macOS |
Tweetable Exploit Released
As this blog post described a generic sandbox escape vulnerability in macOS’s /usr/bin/open utility, a command commonly used to launch files, folders, and applications just as if a user double-clicked them. While open is a handy command, it doesn’t create child processes on its own. Instead, it performs an inter-process communication (IPC) with the macOS Launch Services, whose logic is implemented in the context of the launchd process. Launch Services then performs the heavy lifting by resolving the handler and launching the right app. Since launchd creates the process, it’s not restricted by the caller’s sandbox, similar to how MDSec’s POC exploit worked in 2018.
With the above writeups, researchers came up with a proof-of-concept (PoC) that used the -stdin option for the open Command on a Python file to bypass the “com.apple.quarantine” extended attribute restriction.
The PoC code simplifies the exploration by just dropping a Python file that contains arbitrary commands. With open –stdin=’~$exploit.py’ -a Python command runs the Python app with our dropped file serving as its standard input.
 |
| macOS App Sandbox escape Exploit |
The researcher managed to short the above exploit code, which can be tweeted in a single Twitter post.
 |
| Tweetable macOS App Sandbox escape exploit |
Microsoft shares the vulnerability disclosure credit with another researcher, Arsenii Kostromin (0x3c3e), who discovered a similar technique independently. The software giant also recommends macOS users to install these security updates as soon as possible.