
A security consulting and education company, MDSec labs have discovered the misconfiguration and human error called "NotGitBleed", which can simply expose important data and may lead to major security breaches.
Due to configuration errors or human error, significant numbers of people may have accidentally checked GitHub credentials into GitHub commits as metadata, most commonly a username as the author name and a password in the email address field. MDSec estimate that 100,000 users' credentials may have been affected covering a wide range of organizations including governments, corporations, large open-source foundations as well as smaller organizations and individuals.
In the early of this month, GitHub announced it will automatically block accidental secrets exposure to prevent exposure of credentials before committing code to remote repositories. So with this rollout, GitHub will auto revoke PAT tokens and GitHub credentials if they are detected in commit metadata and have performed the task retroactively so any developer on GitHub.com who may have been affected in the past should have received an email already.
How this Leak Arrived?
MDSec says, an unnamed developer, first noticed this form of a credential leak who himself had accidentally committed their username as their committer name and their password as their committer email address. With this incident, researchers came to know that this incident had happened before a number of times over the years, possibly without the users ever knowing they had done this.
Cause of the Leaks
When the developer was setting g up an IDE on his computer for a new project, he got a prompt for a git author name and email address, that looks similar to the login screen. This causes him to enter his credentials which were saved as commit metadata every time they committed to any repo.
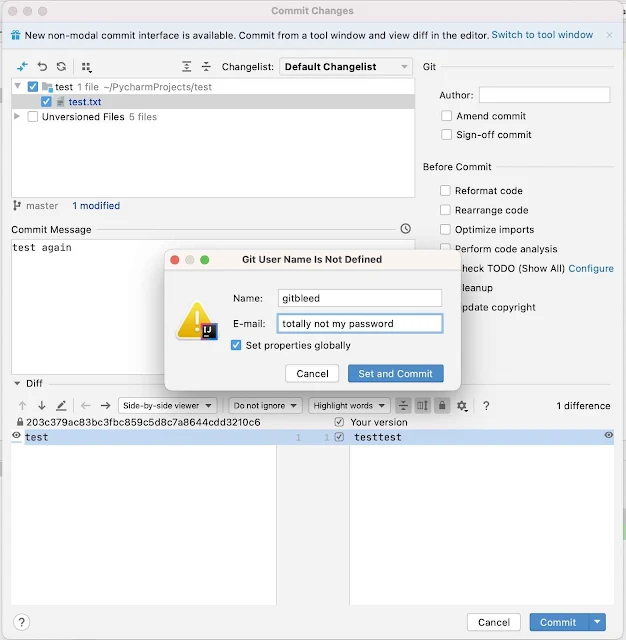
The researcher says that there could be other reasons for this, including bugs in automation scripts and possibly a misunderstanding of the git CLI.
Are you Affected or Not?
MDSec Labs noted that they had done this research "NotGitBleed" only on GitHub and its products. There is possible that other code repository systems are also affected by this or a similar issue, so the researcher has not disclosed any specific details about affected organisations or repos at this time.
Here are a couple of guides by researchers to look for secrets in GitHub commit data -
- Check Git Config
- Check Git log
- Look into GitHub Search.