
Update: Globant confirmed the hacking incident and released a press release.
"We have recently detected that a limited section of our company’s code repository has been subject to unauthorized access. We have activated our security protocols and are conducting an exhaustive investigation."Additionally, Globant mentioned they are present in 18 countries working for companies like Google, Rockwell Automation, Electronic Arts, and Santander, among others.
Hackers have leaked 70GB of data from Globant with the message quoted -
"We are officially back from a vacation."
The below screenshots (shared by hackers), contains the folder of the name of many companies including the big tech ones also as Facebook, Apple Health app, DHL, Citibank, and BNP Paribas. Whether the folders are evidence of client data being exposed is unknown, but the mere fact that internal files appear to have been exposed is embarrassing. Another depicted folder is titled "Arcserve" – perhaps indicating work for the data management vendor of the same name, or possibly just Globant's backups.
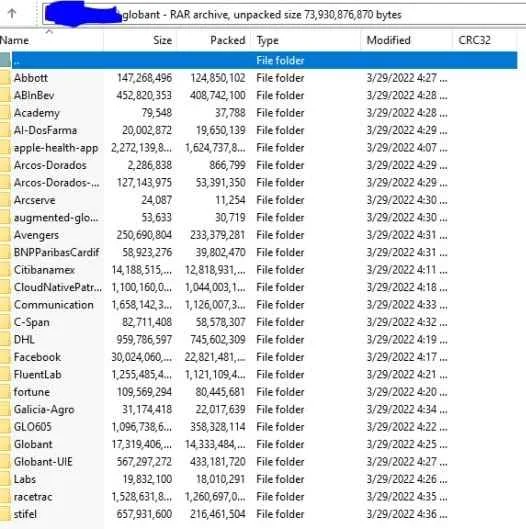
Additionally, the Lapsus group has also published the login credentials of their (Globant) system admins. Furthermore, they also added they will expose the admin credential of all Globant DevOps platforms.
The leak data has been shared via a torrent file containing Globant customer's source code.
Lapsus$, meanwhile, continues to cause trouble for single-sign-on-as-a-service outfit Okta, as new information about the gang's attack has emerged. Security researcher Bill Demirkapi revealed some evidence of the Lapsus$ group. He shares the documents detailing the attack on Sitel.

The documents above are a log of what looks like the attack on Sitel, and detail a logon over RDP followed by a search for "Privilege escalation tools on GitHub". There's also evidence of malware downloads, termination of security software processes, and further skulduggery.
According to the documents, Sitel said it discovered the security incident in its VPN gateways on a legacy network belonging to Sykes, a customer service company working for Okta that Sitel acquired in 2021. The documents also detail, the hackers accessed a spreadsheet on Sitel’s internal network early on January 21 called “DomAdmins-LastPass.xlsx.” The filename suggests that the spreadsheet contained passwords for domain administrator accounts that were exported from a Sitel employee’s LastPass password manager.