
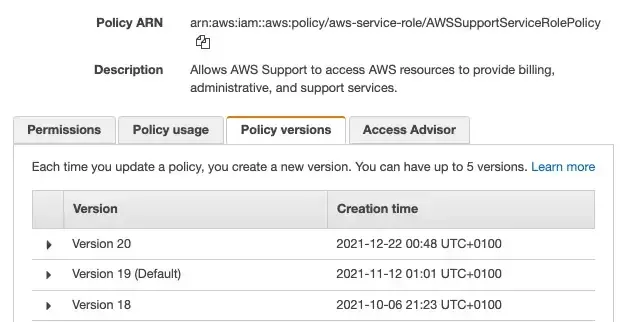
Last Wednesday, Amazon AWS supports team deployed a new version of AWSSupportServiceRolePolicy v20, used by a mandatory role for AW Support access to all AWS Accounts. In this policy, they added the action: s3:getObject which gives access to all customer data by AWS Support teams.
Later some hours AWS team have reverted the change and made the v19 version (old version) the default version for everyone. When the AWS security guys detected the change of AWSSupportServiceRolePolicy they came up with the awareness tweet.
Victor Grenu, an independent AWS cloud security with a Twitter handle @zoph twittered about the changing incident that took place in AWS cloud with the warning message -
The day when the AWS Support got access to your S3 data.
— Victor Grenu (@zoph) December 23, 2021
In this thread, you will find details about the security incident that leads to this unattended access for millions of AWS customers. 🧵
Further, he added- users can't delete the Support role and also cannot use SCPs on service-linked-role.
After this, the Amazon AWS team released a statement regarding this unexpected behavior.
Between December 21, 2021 at 23:48 UTC and December 22, 2021 at 08:23 UTC, the policy used by AWS Support automated systems - AWSSupportServiceRolePolicy - inadvertently included S3:GetObject permissions. This change has been reverted. While these permissions were temporarily present, they were not and could not be used - only a tightly controlled set of AWS support systems may assume the AWSSupportService role, and these systems do not provide the capability to access S3 objects even if permission is granted to the role.
AWS team mentioned that the support team cannot access the user's S3 buckets - "systems do not provide the capability to access S3 objects even if permission is granted to the role".
What to do to Secure your S3 Bucket
To prevent unattended access from the AWS Support team, users can perform a couple of things-
- You should enable CloudTrail S3 Events (it could be costly for accounts with a lot of S3 object movements).
- Enable server access logs - you will not have a full picture here as some info is missing.
- You can use KMS-CMK to control access.
- You can limit resource policy (buckets).