
There is no denying the fact that data today acts as a key asset! And no matter how big or small or medium-sized your business is, you must protect your asset. In the present times, outsourcing and offshoring have gained quite a lot of momentum, and businesses are often found seeking reliable offshore developers. Here is a small guide that focuses on what is data security and the significance of data security, especially when dealing with an offshore software development company.
What is Data Security?
As the name implies, data security is more like a safe locker where you can protect your valuable data and information from irrelevant and unauthorized access for your entire tenure. Security breaches have been making huge headlines a lot lately. Some of the most successful and trustworthy companies have been hacked. It’s a huge loss not just for businesses but also for their valued customers.
Before proceeding further, I would like to mention certain reasons why businesses must consider data security in any manner whether it’s in-house or offshore software development.
Importance of using Data Security
1. Being hacked is not acceptable
As a business don’t you think it’s your prime responsibility to perform due diligence when it comes to their client and employee records and transactions. If not done accurately, all this might result in several negative consequences such as financial costs, loss of public trust, damaged brand reputation, a huge impact on future profits, and maybe Legal or regulatory consequences associated with breaches.
With data security, one can at least prevent unauthorized access. The advanced technology hasn’t just given businesses an opportunity to grow but at the same time giving bad guys the power to evade security measures in no time. If you are putting no interest in security by 2021, it surely means you are inviting trouble by leaving front doors open for hackers to get in and explore your vulnerabilities via computers, laptops, websites, networks, peripheral equipment, and so on. Adding increased layers of information security will go a long way in deterring unauthorized access to business systems and equipment.
2. Curtail Unnecessary Expenses
Another astounding reason for incorporating data security is you will be able to cut unnecessary expenses. I mean when you are vulnerable to cyber attacks or do not invest in data security what happens is that you lose financial documents, employee information, and confidential client files which are way more impactful than those monetary losses. Moreover, trust and reliability might get deteriorated in the eyes of both your existing and potential clients.
Clearly, investing in data security measures safeguards the future of your firm and keeps you on the path of the uninterrupted economic process.
3. Enhances Brand Reputation and Cultivates Loyalty
It takes long days and even longer nights to build a reputation, and all it takes is one moment of recklessness and everything is finished. Any potential data breach would not just risk you hefty fines, but would also pose a threat to the security of your clients and thereby, the future of your business.
Data security is a must!
How to Manage Data Security While Working with an Offshore Software Development company?
Recently, two concepts have been popping up like never before. One is offshore software development and the second is global data breaches. Both are inevitable! It may quite interest you to know that a tech community discovered that the Japanese messenger app Line has been leaking its user data to china for almost a couple of years. As a result, not just companies but customers have become more concerned when it comes to sharing their vital information.
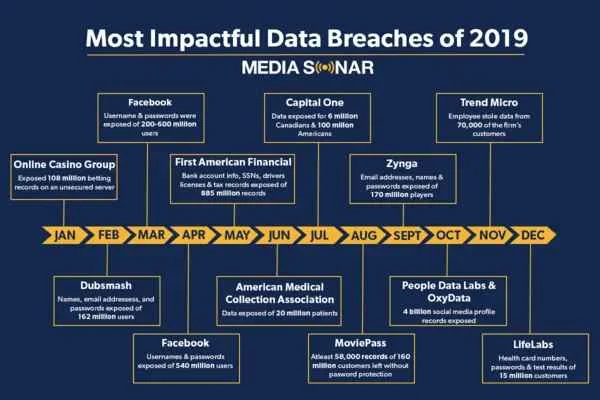 |
| Source: colocationamerica.com |
Call it a boon or a bane, this is how it is! After the pandemic, companies are bound to consider offshore software development even if data security is one of their prime concerns. What choice do they have other than to delve into?
Apart from that, it has been more than a decade since we have been hearing horror and exaggerated stories of offshore security breaches. This has totally left businesses questioning the security of their confidential data with their remote team.
Engaging remote employees is not a new norm anymore. With so many vendors in play, this has driven prices further down and made the market extremely competitive, which means that businesses who are outsourcing have profited immensely. However, it doesn’t mean all this is a cakewalk. In fact, I hear about clients running into trouble with offshore teams, suffering data theft, and getting defrauded once in a while.
Further below I would like to mention what data security measures you must consider especially when working with an offshore development company.
1. Secure Network Monitoring
As a business owner, it is your responsibility to set up a secured network. Non- tech-driven businesses often ignore the importance of expanding configuration management and dealing with the ever-changing networks. Here you have to ensure that your chosen offshore software development service provider has an updated network. Also, double-check if their security is up-to-the-mark or not. The question is how?
- See if their employees carry specialization in cybersecurity
- Have they already installed updated antivirus software?
- Do they use a firewall?
- Do they download and install OS and application software updates?
- Have they even bothered about creating backups of valuable business data?
- Are their Wi-Fi networks secured?
2. Access to Sensitive Data is a big No!
Remote working conditions increase the possibility of theft and malfunction.
- Develop a separate repository for your offshore team. Put only the information necessary for completing tasks. Ensure the offshore team notifies you before accessing any information.
- Do not provide access to other company data. Monitor additional activities.
- Organize different levels of employee access within the offshore team.
- Encourage a culture of responsibility among offshore staff. Each worker should take responsibility for his/her actions.
- Relocate offshore specialists to your office when dealing with sensitive data. This helps you control all processes and communicate directly.
3. Secure all applications and devices
Is the IT infrastructure configured correctly to ensure the cybersecurity of operations? Installing security patches and updating the security software on all endpoints provides a personal firewall, applicational control, antivirus protection, and antispyware protection.
As a result, hackers won’t be able to access IDs and passwords or use official systems. At the same time, computer and external hard drives are encrypted to protect worker endpoints from unwanted access. At the same time, restrict system access to specific networks or locations. And if any employee desires to log in from a different site, they can do so only once their network/location is authenticated. This mitigates risk and ensures the early detection of a hacking attempt.
Consider implementing a customer identity and access management (CIAM) solution if you use customer-facing applications. It will help you manage digital identities and increase authentication requirements for high-risk logins.
4. NDA
When working with an offshore software development company, just make sure to sign an NDA in advance. And just signing isn’t enough. Do they follow the rules, especially of the country they are based in? In case, if the chosen company restricts itself from signing an NDA, it would be prudent enough to look for another one.
5. All boils down to choosing the right offshore software development service provider
Of course, when you choose the right offshore partner, nothing can go wrong! After all, they won’t just provide you best possible outcomes but also ensure that all cybersecurity measures are in place. Furthermore, they might tailor security measures based on your business requirements, such as mirroring the protocols you use at home and providing cybersecurity training modules to all your employees.
Data Security is not one’s responsibility!
It doesn’t matter whether you are working with an onshore or offshore software development team, data security is everyone’s responsibility. I hope the following post was helpful With those simple tips mentioned above, together we could curb or eliminate threats to your data.