Security researcher Ryan Pickren had discovered a critical security bug on Mac Safari browser and iPhone Safari browser which leads to hijacking users camera of Mac and iPhone.
In short, Ryan explains that the vulnerability allowed malicious websites to masquerade as trusted websites when viewed on Desktop Safari (like on Mac computers) or Mobile Safari (like on iPhones or iPads). The cause of the bug is the feature on Apple browser which lets users permanently save their security settings on a per-website basis.
For successful exploit of the bug, the attacker tricked Apple into thinking a malicious website was actually a trusted one. It did this by exploiting a series of flaws in how Safari was parsing URIs, managing web origins, and initializing secure contexts.
You can read the full technical details about the bug from his blog.
In short, Ryan explains that the vulnerability allowed malicious websites to masquerade as trusted websites when viewed on Desktop Safari (like on Mac computers) or Mobile Safari (like on iPhones or iPads). The cause of the bug is the feature on Apple browser which lets users permanently save their security settings on a per-website basis.
For successful exploit of the bug, the attacker tricked Apple into thinking a malicious website was actually a trusted one. It did this by exploiting a series of flaws in how Safari was parsing URIs, managing web origins, and initializing secure contexts.
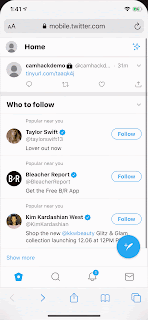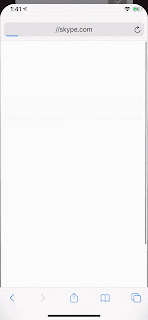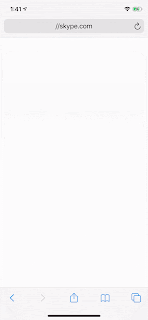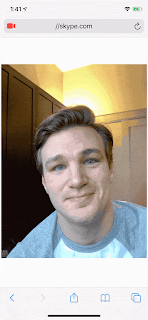
If a malicious website strung these issues together, it could use JavaScript to directly access the victim's webcam without asking for permission. Any JavaScript code with the ability to create a popup (such as a standalone website, embedded ad banner, or browser extension) could launch this attack.During his researcher, Ryan uncovered seven zero-day bugs on Safari browser which are identified as (CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, & CVE-2020-9787), in which he needs to chain three of these bugs to hijack the Apple users camera.
You can read the full technical details about the bug from his blog.
Proof-of-Concept
For these all bugs, Apple rewarded Ryan $75,000 under Mac bounty program. And the hijacking of camera bug was considered into the Network Attack without User Interaction: Zero-Click Unauthorized Access to Sensitive Data.